Code Security on IBM i
How to use CVEs to protect the security of your IBM i application?
For the last six years, security has remained the top concern for IBM i shops when planning their IT environment. Yet IBM i is one of the most secure platforms ever made for business. It has five progressively impenetrable levels of security built deep into the operating system. So, is this security concern really warranted?
Today, as IBM i applications are modernized and integrated with external apps and devices, traditional RPG logic is exposed as Web or microservices – creating a whole new set of risks such as SQL injection and unsafe APIs. For organizations to continue to leverage the value in their proven IBM i assets, a new rigor is needed around the subject of security.
What are CVEs and how do they apply to IBM i applications?
To help organizations face growing security risks, the Common Vulnerabilities and Exposures (CVE) nonprofit program was launched to catalog software vulnerabilities into a public and freely available “dictionary”. Each CVE lists a specific vulnerability or exposure and uses a Common Vulnerability Scoring System (CVSS) is used to evaluate the ‘threat level’.
Each vulnerability is assigned a CVSS base score between 0.0 and 10.0 — a score of 0.0 represents no risk and 9.0 – 10.0 is a critical risk score..
How to identify these security risks?
DevSecOps has made security a shared responsibility throughout the entire IT lifecycle. Continuous security checks are now built-in to the application development process.
Designed specifically for IBM i, ARCAD CodeChecker is a key element of any DevSecOps implementation. ARCAD CodeChecker automates the detection of security vulnerabilities in RPG and CL code. It acts as a standalone ‘quality gate’ that can plug into any DevOps cycle.
ARCAD CodeChecker integrates with RDi making it easy for developers to check for security flaws as they code. You can also use ARCAD CodeChecker with Jenkins to automate standard IBM i security checks withing a standard CI/CD pipeline.
How does ARCAD CodeChecker work?
ARCAD CodeChecker works by analyzing source code against a set of rules, metrics, and metric models. Industry standard rules are provided out of the box which can be customized or enhanced for local requirements. Each security rule in ARCAD CodeChecker maps through to a single or multiple CVEs, or in some cases be independent of any CVE.
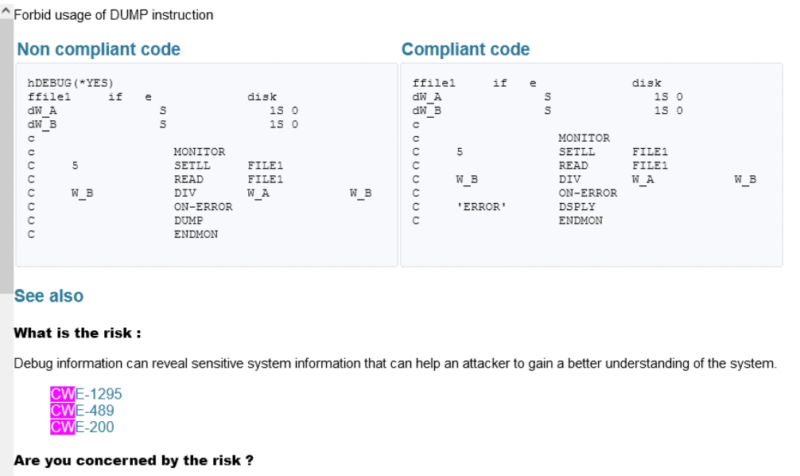
ARCAD CodeChecker reports on how your source code complies with, or violates, the rules defined. To help you assess your level of vulnerability or exposure and learn the appropriate corrective measures to apply, ARCAD CodeChecker also documents each rule violation, including:
How to report on security risks in your IBM i application?
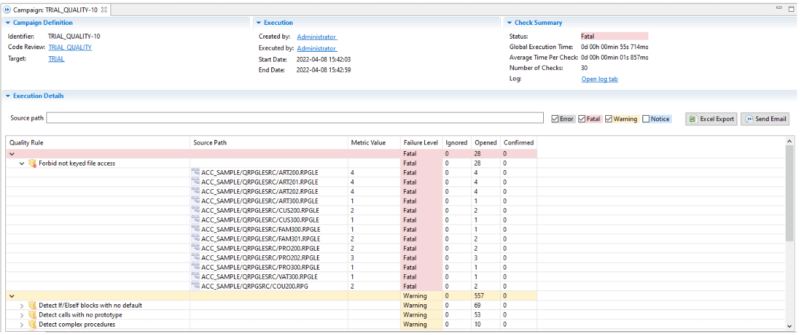
ARCAD CodeChecker generates a campaign results report, organized by severity. According to the rulesets you have chosen for your campaign, the results report will deliver a high-level, summary view of the quality violations and security vulnerabilities identified.
Click from the report to specific rule documentation to understand the cause of the violation and the recommended course of action, including external CVE links.
The security results report gives an easy and rapid way to determine “am I at risk?” and prove your compliance to both industry-wide and local coding standards on IBM i.
How can I anticipate the security risks I face?
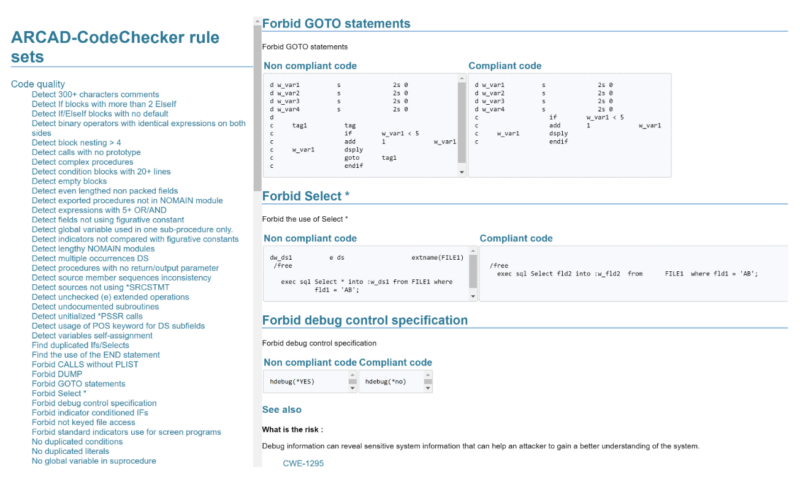
To help you learn more about new security risks – ARCAD CodeChecker allows easy browsing of rule documentation, categorized by rule set.
Using ARCAD CodeChecker rule documentation, developers can rapidly inform themselves of coding best practices on IBM i and the constructs to avoid.
Thanks to the specific IBM i knowledge contained within ARCAD CodeChecker and the quick links to external CVEs, organizations can rapidly take preventive action to safeguard the security of their business-critical IBM i source code and data.
How to safeguard application security on IBM i?
Get ARCAD CodeChecker!

REQUEST A DEMO
Let’s talk about your project!
Speak with an expert